Preventing Exposure Before It Becomes Backlog: Introducing Averlon Precog
Modern infrastructure teams manage highly dynamic, distributed systems where small network configuration changes can materially affect service availability and security posture. Changes to security groups, DNS records, routing rules, firewall policies, or access control settings are routine parts of infrastructure operations. However, without proper visibility and validation, these changes can easily lead to significant outages or security exposures.
Real-World Examples of DNS and Configuration Failures
There have been multiple recent high-impact incidents where relatively small changes in network configuration infrastructure caused major service disruptions:
- AWS DNS Resolution Failure (October 2025). On October 20, 2025, Amazon Web Services experienced a major outage rooted in a DNS resolution problem affecting the DynamoDB service endpoints in the US-EAST-1 region. This DNS failure prevented clients from resolving critical addresses for internal services. As a result, many dependent services, including customer applications across industries, became unavailable for hours. The DNS issue cascaded into failures of additional AWS components before engineers manually remediated the condition.
- Microsoft Azure Front Door Configuration Change (October 2025). Microsoft suffered a global outage when a configuration change to Azure Front Door triggered a DNS failure that made numerous Microsoft services unreachable. Impacted systems included the Azure Portal, Microsoft 365 admin interfaces, and authentication services. Engineers had to block all further configuration changes and roll back to the last known stable configuration to restore service.
There are also well-known historical events that relate directly to routing and name resolution changes:
- Facebook BGP/DNS Outage (2021). A single routing configuration update inadvertently withdrew routes to Facebook’s authoritative DNS servers, making Facebook, Instagram, WhatsApp, and related services unreachable for users worldwide until engineers could manually reset systems.
These incidents illustrate how DNS and configuration changes, not application bugs or code defects, can lead to widespread outages.
Modern cloud environments are defined by continuous change. Every update to a security group, routing rule, IAM policy, or DNS configuration modifies the system’s attack surface. The risk does not enter through static code alone. It enters through change.
TL;DR: Modern infrastructure risk enters through change. Averlon Precog evaluates exposure impact during proposed infrastructure updates to prevent new production risk and slow vulnerability backlog growth.
Security Group Changes and Overlooked Security Misconfigurations
Misconfigured security groups and firewall policies remain one of the top vectors for both outages and security risk. For example:
- Security group rules that are too permissive can inadvertently expose internal systems to the public internet or lateral movement by attackers.
- Conversely, overly restrictive rules can block legitimate service traffic, causing application failures.
- Incorrectly deployed network ACLs have repeatedly been implicated in cloud outages that could have been prevented with better pre-deployment validation.
Industry research consistently ranks security misconfiguration, including network controls, among the leading causes of breaches and service outages.
Engineering and Security Team Coordination Challenges
Engineering and security teams have differing priorities:
- Engineering teams focus on speed of delivery, frequent iteration, and rapid deployment.
- Security teams focus on resilience and risk mitigation, ensuring that changes do not introduce vulnerabilities or violate policy.
Without shared tooling, teams operate with asymmetric visibility:
- Engineering may deploy changes that unintentionally violate security policies or break network reachability.
- Security teams often discover risky changes only after review processes or, worse, after an outage or exposure has occurred.
- Security teams may issue warnings late in the development cycle, causing rework, delays, and frustration.
This disconnect increases incident risk and leads to repeated firefighting, late feedback, and strained team relationships.
Exposure Enters Through Change
Security teams are typically notified after deployment, when scanners or monitoring systems detect a new issue. By that point, the change has already been merged, applied, and propagated.
Infrastructure changes are not inherently risky. The challenge is that their impact on exposure is rarely evaluated in context before they are introduced. Without contextual reasoning, teams default to reactive detection rather than preventative exposure analysis.
What Preventative Exposure Reasoning Looks Like in Practice
Preventative exposure reasoning requires evaluating proposed changes in the context of existing infrastructure, vulnerability posture, and reachable attack pathways.
Averlon Infrastructure Precog is designed to bring shared visibility, automated risk detection, and actionable context directly into the change workflow before changes are applied. Precog integrates into existing CI workflows, evaluating infrastructure changes as part of the pull request process so exposure impact is understood before merge.
Precog is not static linting and it is not simple rule enforcement. Traditional policy tools validate configuration syntax or enforce predefined guardrails. Precog evaluates proposed infrastructure changes in the context of existing cloud state, vulnerability posture, and exposure paths. It reasons about how a change alters reachable attack surface and operational risk, not just whether a rule is violated. Concretely, this capability shows up in four ways:
- Pre-Change Analysis and Visibility
Precog evaluates proposed network and infrastructure changes (security groups, DNS updates, route modifications) before they are merged. This gives both engineers and security reviewers insight into the potential impact of a change.
- Automated Risk Insights
Through automated policy checks and contextual heuristic analysis, Precog identifies risky patterns such as overly permissive security group rules or DNS changes that could break resolution paths.
- Shared Context Across Teams
Engineers see security-relevant information early in the development pipeline. Security teams receive structured summaries that provide context without needing to manually interpret every diff.
- Audit-Ready Documentation
Precog produces change summaries that document the intent, risk classification, and reasoning behind network adjustments. This supports compliance and post-incident reviews.
By surfacing impactful infrastructure changes early and providing actionable risk indicators, Precog aligns engineering velocity and security assurance. Teams can act on the same authoritative source of truth rather than relying on after-the-fact reviews or reactive incident response.
Let’s walk through an example of this:
- Imagine you have done internal validation of your service and ready to make it accessible to production and thereby making the security group change to make the service accessible over internet:
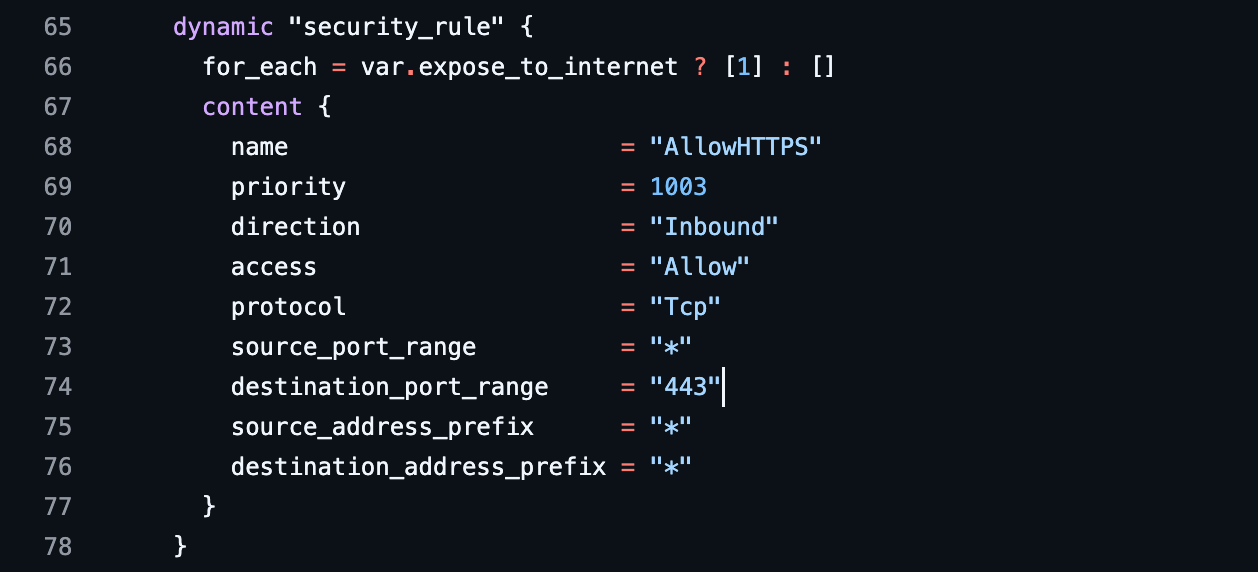
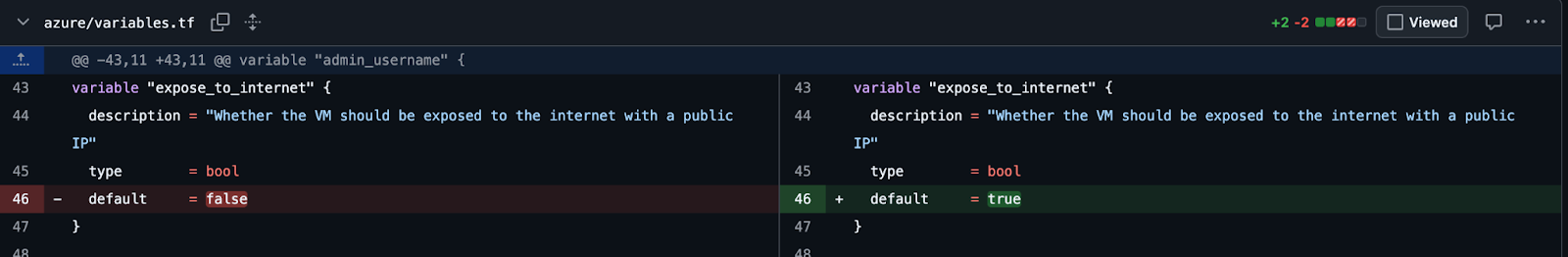
- Averlon’s Terraform Precog agent is able to use the changed state in your Terraform and existing cloud deployment to figure out if something new is going to get exposed or not:
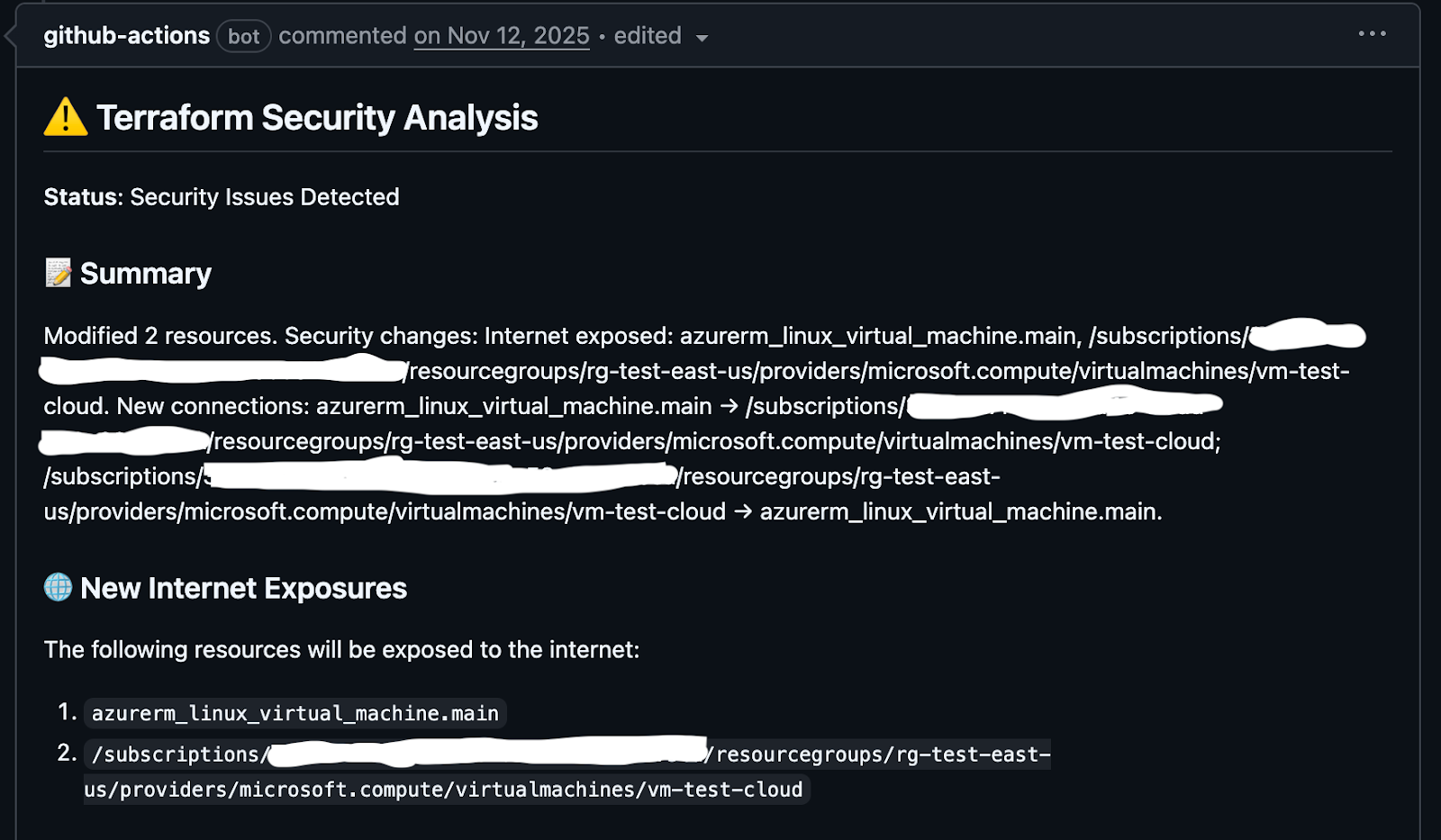
- After determining changes in network exposure, Precog provides the risk carried by the workload:
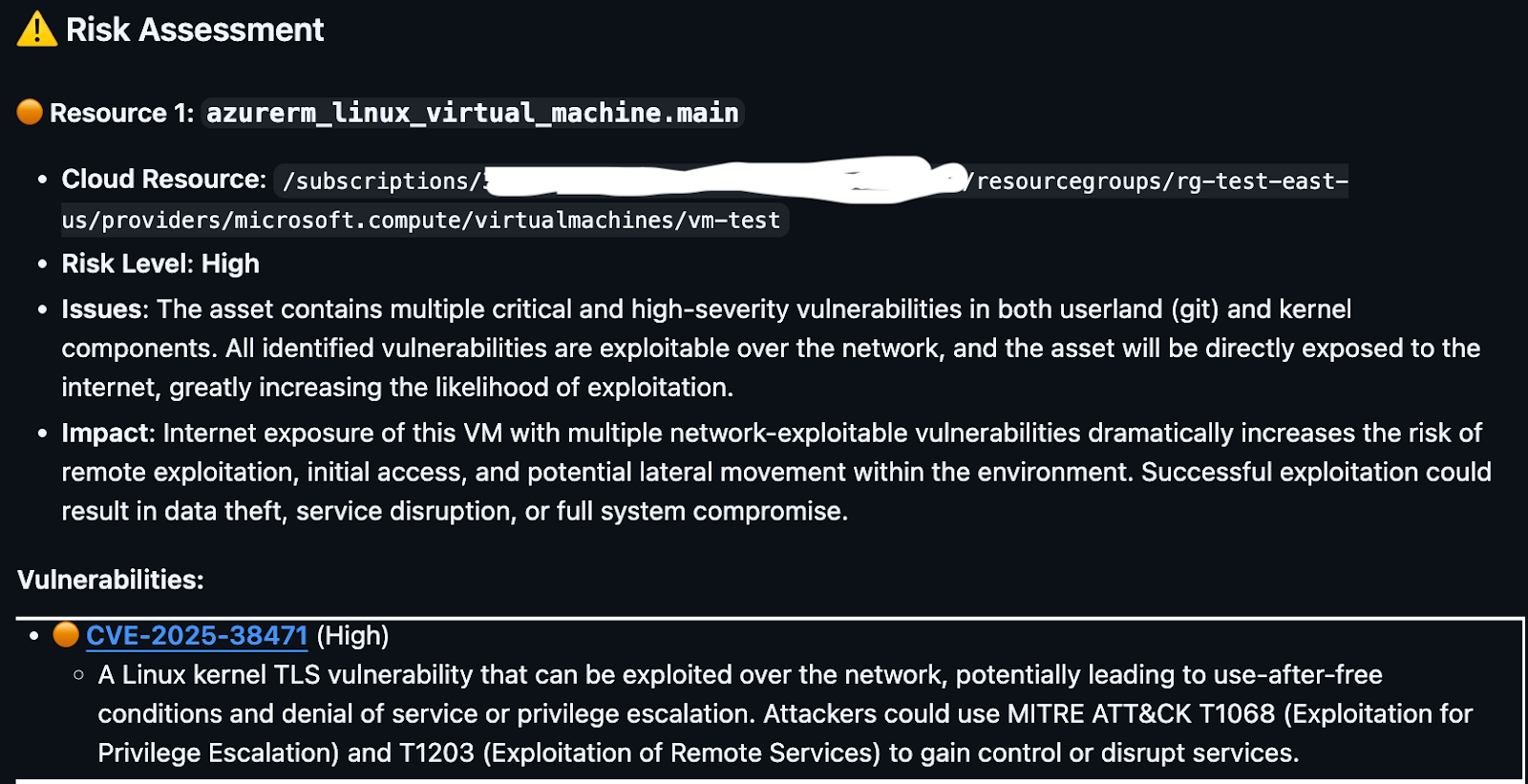
This is where configuration risk and vulnerability risk intersect. A previously contained vulnerability becomes materially exploitable when exposure changes. Evaluating that intersection before merge is what prevents avoidable escalation.
Preventing Exposure Before It Becomes Backlog
Modern infrastructure will continue to evolve. Security groups, DNS records, routing policies, and identity boundaries will change. The question is not whether change will occur. It is whether its exposure impact is understood before it propagates into production.
When exposure is evaluated only after deployment, security teams are forced into reactive remediation. Findings accumulate. Backlogs grow.
By reasoning about impact at the point of change, before merge, teams reduce the number of issues that ever become production exposure.
Evaluating exposure before merge reduces backlog growth. Intelligent remediation reduces the backlog that already exists. Precog operates at the moment of change. It ensures risk is evaluated before it becomes something that must later be fixed.
Featured Blog Posts
Explore our latest blog posts on cybersecurity vulnerabilities.
Ready to Reduce Cloud Security Noise and Act Faster?
Discover the power of Averlon’s AI-driven insights. Identify and prioritize real threats faster and drive a swift, targeted response to regain control of your cloud. Shrink the time to resolution for critical risk by up to 90%.