From Findings to Fixes: Closing the Cloud Exposure Window with Upwind + Averlon
Modern cloud environments generate more findings than teams can handle. Security leaders are flooded with alerts but lack the context to know which vulnerabilities are exploitable or how to fix them efficiently.
Adversaries are exploiting vulnerabilities faster than before. The average time to exploit a disclosed vulnerability has dropped to 5 days and continues to accelerate. At the same time, remediation often lags. The median time to remediate Known Exploited Vulnerabilities (KEV) is 174 days.
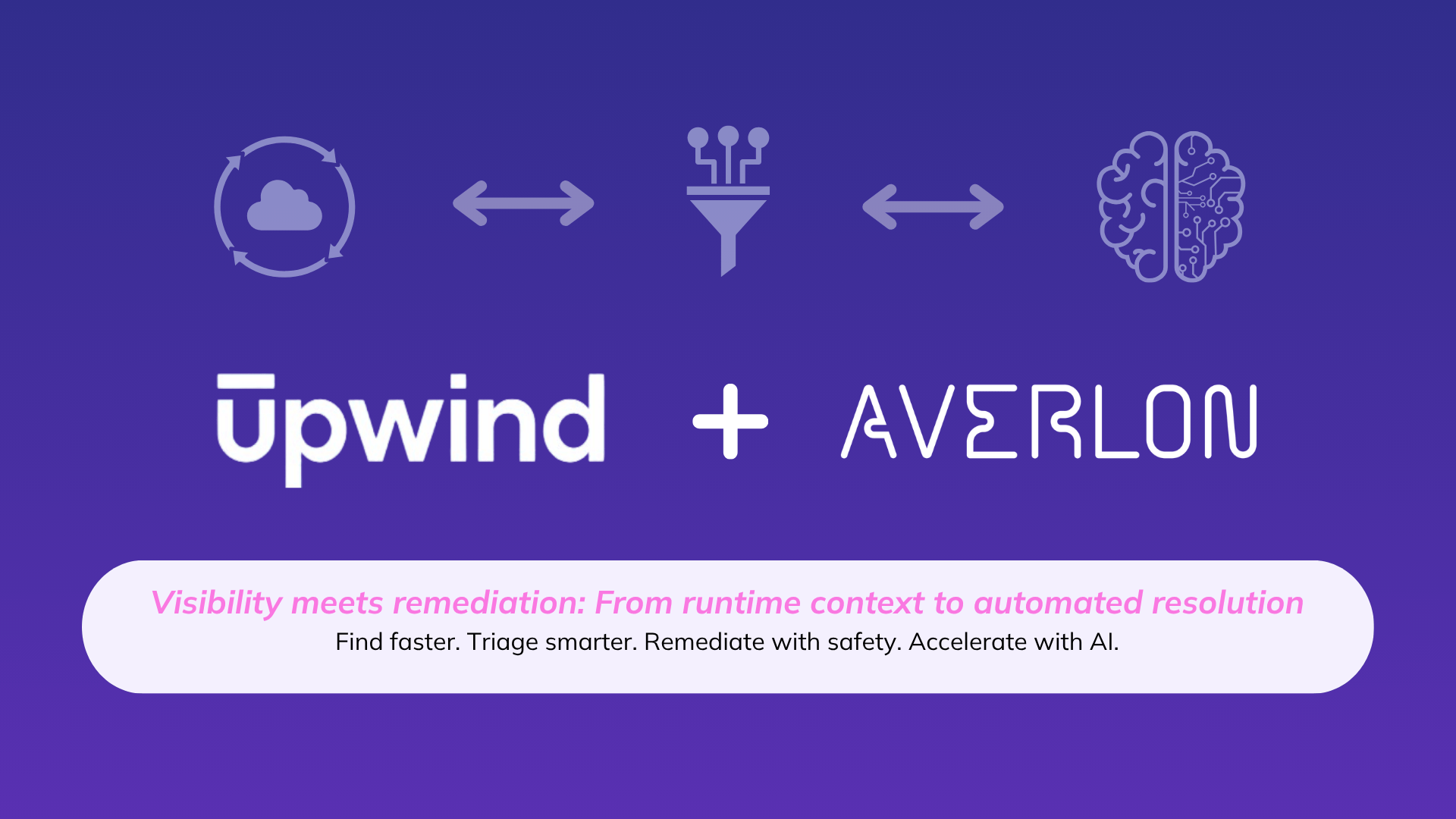
The result is an expanding exposure window that attackers can use to their advantage. Upwind and Averlon work together to narrow that window by combining cloud-wide context with engineered remediation to focus effort where it matters.
Why Upwind + Averlon Matters
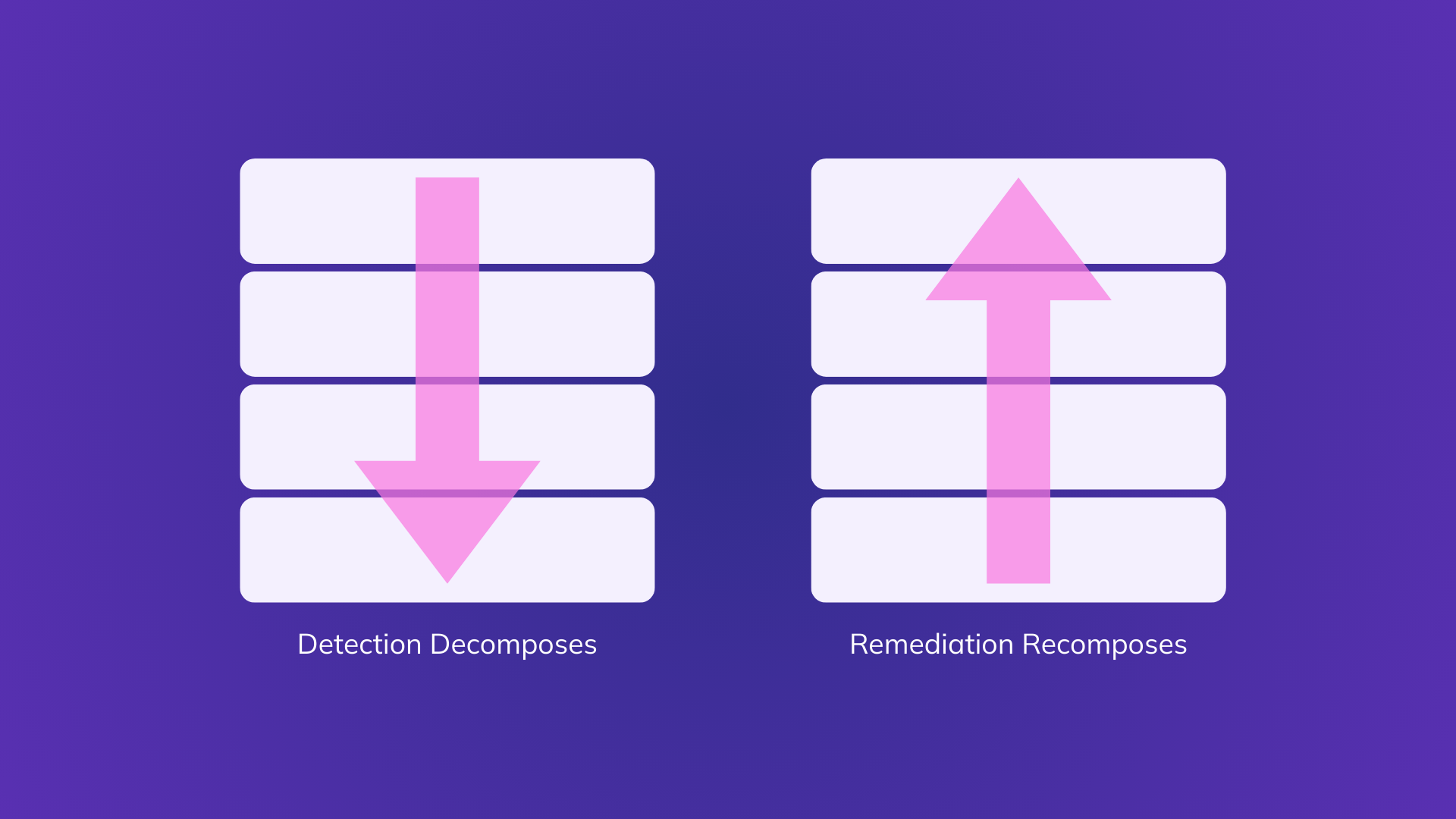
Security teams detect risks across cloud workloads, identities, and applications faster than they can resolve them. What often slows them down is fragmented context, knowing something is wrong but not knowing if it is exploitable or how to fix it.
Upwind provides a full cloud security platform that combines posture management, vulnerability management, and runtime protection. Built with eBPF technology, it gives a real-time, inside-out view of workloads, network activity, and application behavior, while also correlating that data with cloud configuration and identity context. This context helps pinpoint which issues represent live, exploitable risk rather than theoretical findings.
Averlon aggregates findings from Upwind and other connected sources, analyzes exploitability, and prioritizes issues based on impact and context. It then generates actionable remediation plans and automates delivery into developer workflows, safely implementing fixes and accounting for potential breaking changes.
Together, Upwind and Averlon give teams clear visibility into what matters most and the automation to act on it, helping them close the exposure window faster and more reliably.
How the Integration Works
Together, Upwind and Averlon create a connected workflow from detection to fix.
1) Ingest and Enrich
Averlon connects to Upwind to ingest vulnerability findings, posture data, and runtime signals. Upwind’s runtime fabric, built on eBPF, observes workload and process behavior without sidecars or code changes, providing high-fidelity telemetry.
Averlon enriches those findings by connecting directly to customer cloud environments and other integrated tools. This consolidation maps each finding to its corresponding cloud asset, account, or environment and creates a single dataset for assessing exploitability and prioritization.
2) Assess Exploitability
Averlon evaluates exploitability using multiple context layers to determine whether a finding represents real and reachable risk:
- Runtime insight (from Upwind): Identifies whether the affected workload or process is actively running, adding live operational evidence that helps confirm relevance.
- Package applicability: Evaluates whether the vulnerability applies based on the component’s functional role in the environment, ensuring only relevant issues are surfaced for remediation.
- Reachability analysis: Determines whether the vulnerable component is actually reachable by analyzing network configurations, IAM policies, and Kubernetes RBAC and network policies.
For example, a vulnerable library might not be present in any deployed container, or a package with a known issue might be irrelevant in a headless environment. Averlon uses that context to deprioritize the vulnerability.
Together, these signals help Averlon distinguish theoretical vulnerabilities from those that can be exploited in real-world conditions.
3) Prioritize with Attack Chain Analysis
Averlon maps identified vulnerabilities and misconfigurations into attack chains that show how an attacker could progress from entry to impact. Prioritization is driven by this analysis, surfacing issues that sit on critical paths to damage so teams can focus remediation where it has the greatest effect.
4) Actionable Remediation in Developer Workflows
Once priorities are established, Averlon automatically generates contextual remediation and routes them directly into developer workflows such as pull requests (PR), IDE environments, or CI/CD workflows. Every remediation includes the evidence behind its prioritization and clear guidance on how to fix or mitigate the issue safely, including automatically addressing breaking changes.
What You Can Achieve with Upwind + Averlon
Together, Upwind and Averlon deliver measurable outcomes that help security and engineering teams close the exposure window with greater speed, precision, and confidence.
- Shrink the exposure window by focusing on vulnerabilities that are both exploitable and impactful.
- Reduce vulnerability noise with runtime- and posture-informed context that aligns fixes to what is actually happening.
- Accelerate remediation by delivering engineering-ready fixes within developer workflows while automatically addressing breaking changes.
- Increase confidence with traceable evidence and safeguards that ensure every prioritized fix is both effective and safe to deploy.
- Adapt to modern cloud environments with posture and runtime insights from Upwind feeding directly into Averlon’s remediation engine.
The result is a measurable reduction in the time between findings and fixes, helping teams keep pace with the speed of modern threats.
Who This Helps
- Cloud security and vulnerability management teams who need to focus effort on what is actually exploitable.
- DevOps, platform, and application teams who want clear, contextual fixes delivered directly into their workflows.
- Security operations teams who aim to connect detection with remediation.
- Security leaders and CISOs who want measurable progress in reducing exposure and improving mean time to remediation.
Next Steps
If you already use Upwind, connect your workspace in Averlon to bring posture and runtime context into exploitability assessment and prioritization.
If you already use Averlon, enable the Upwind connector to enrich findings with runtime visibility and cloud context.
- Solution brief: (coming soon)
- Learn more: Averlon platform
- See it live: Request a demo
Featured Blog Posts
Explore our latest blog posts on cybersecurity vulnerabilities.
Ready to Reduce Cloud Security Noise and Act Faster?
Discover the power of Averlon’s AI-driven insights. Identify and prioritize real threats faster and drive a swift, targeted response to regain control of your cloud. Shrink the time to resolution for critical risk by up to 90%.