FedRAMP’s Push for Faster Vulnerability Remediation: What RFC 0012 Means for Security Leaders
.png)
1. Why This Matters Now
FedRAMP’s new proposal for RFC 0012: Continuous Vulnerability Management Standard could reshape how federal cloud providers — and the teams who secure them — handle vulnerabilities.
RFC 0012 lays out clear, severity-based timelines for remediation and tighter expectations for how exploited or exploitable issues are prioritized. It moves away from ambiguity and informal risk acceptance, signaling a shift toward measurable action and faster response.
If you build, operate, or secure systems in a FedRAMP context, this change affects you.
2. What’s in RFC 0012: Remediation Timelines at a Glance
At the core of RFC 0012 is a straightforward framework: fix vulnerabilities faster, based on how severe — and how exploitable — they are. According to Section 3.1 of the RFC:
The RFC also includes specific guidance for vulnerabilities with heightened risk:
“When a vulnerability is determined to be actively exploited or a public exploit is available, it must be remediated according to the timelines for Critical or High vulnerabilities.”
This means exploit status affects how quickly you must act — even if the CVE was previously scored as Moderate or Low. If a vulnerability has a public exploit or is being actively used in the wild, you must reclassify it as High or Critical to meet the stricter response timelines.
3. FedRAMP’s Broader Expectations: Beyond Faster Fixes
RFC 0012 doesn’t just propose new timelines — it introduces a broader Continuous Vulnerability Management standard (FRR‑CVM) that applies at all times to all FedRAMP-authorized systems. These requirements formalize how providers must detect, assess, report, and remediate vulnerabilities — not occasionally, but as a sustained, auditable process.
Key expectations include:
- Credible exploitability analysis based on reachability, applicability, and context
- Transparent reporting — machine-readable and traceable from discovery to closure
- Use of automation where possible, especially for internet-exposed assets
- Defined scan cadences for both external and internal environments
- Strict timeframes — as short as 3 days for exploitable issues, with all vulnerabilities addressed within 6 months
For cloud providers and their security teams, this isn’t just about compliance. It’s a shift toward measurable, continuous assurance — and it raises the bar for remediation programs across the board.
4. From Proposal to Policy: What’s the Process?
RFC 0012 is open for public comment through August 14, 2025. After that, FedRAMP’s Program Management Office (PMO) will review feedback, refine the draft, and may incorporate it into future baseline documentation.
In short: this isn’t final yet — but it’s directionally important. Smart teams will use this moment to tune their remediation pipelines before enforcement begins.
5. Not Just Fixing — Understanding When the Clock Starts
While most of the attention is on remediation deadlines, RFC 0012 also lays out what happens before the timer starts.
The “Quick Reference – Discovery and Analysis Time Frames” section outlines the process organizations should follow after discovering a vulnerability:
- Create a ticket in the tracking system
- Assess the vulnerability’s impact
- Assign a severity rating
🟡 RFC 0012 does not define strict time limits for these steps — but the expectation is clear: classification should happen promptly, so remediation can begin on time.
Waiting to assess or assign severity doesn’t pause the risk — and may affect your ability to comply.
6. From Exploitability to Action: How to Prioritize What Matters
Not all vulnerabilities are equal — and treating them as such creates waste, delay, and blind spots.
The most effective remediation programs assess exploitability as a first pass:
- Reachability: Is the vulnerable component accessible to an attacker?
- Applicability: Is the vulnerable code path actually in use in this deployment?
A critical vulnerability in a cloud service in a package that requires user interaction is not the same as a moderate issue in a public-facing service with an active exploit.
But exploitability alone isn’t enough. Prioritization must also consider:
- How the issue fits into a broader attack chain
- Whether existing controls or mitigations are in place
- The potential impact on data, operations, or mission-critical systems
These layers of context allow teams to cut through volume and focus on what truly demands attention — especially when timelines are tight.
7. Agentic RemediationOps: From Risk Detection to Fix — Fast
To hit a 3- or 7-day remediation SLA, teams can’t rely on ticket queues, gut feel, or manual reviews. What’s needed is a system that prioritizes, guides, and accelerates remediation without bottlenecks.
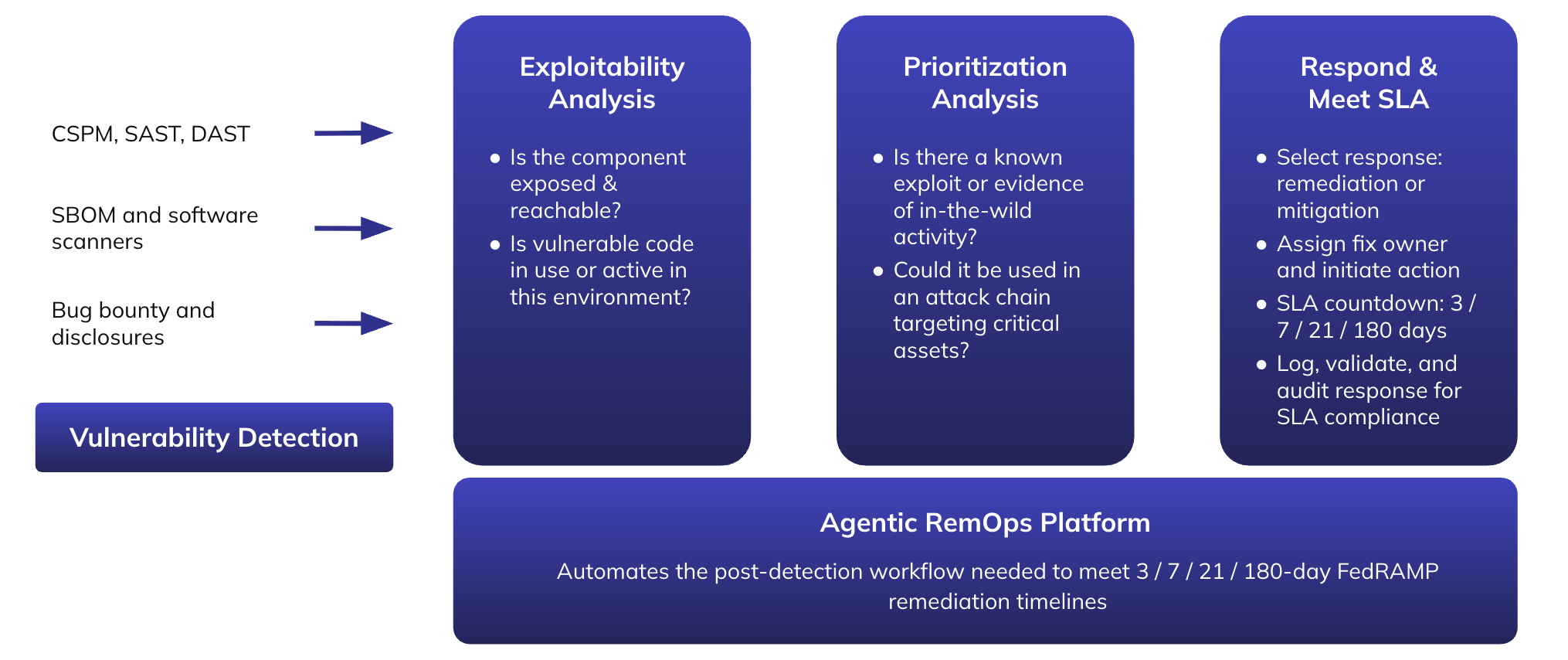
This is the promise of Agentic RemediationOps — a modern, agentic AI-augmented approach that unifies detection, context, and action:
- Exploitability analysis: Understand if the vuln matters, not just that it exists
- Prioritization: Score risk based on attack chain context, not just CVSS
- Remediation & mitigation: Recommend or automate the right remediation step (patch, config, isolation) or provide an appropriate mitigation (WAF policy, privilege management, etc.) to reduce risk exposure
- SLA-aware tracking: Ensure issues are resolved within policy, not just closed
Importantly, this isn’t just automation — it’s agentic automation with judgment, where human approval stays in the loop for high-impact changes.
And it’s built to support everyone: Security, DevOps, Engineering, and Leadership — without needing to reinvent workflows from scratch.
8. Best Practices to Get Ahead
To prepare for the timelines and expectations in RFC 0012, here’s what we recommend:
✅ Make exploitability analysis part of triage — not a separate process
✅ Treat exploit intelligence as a trigger — reclassify risk when public exploits are released
✅ Audit current response timelines — how long does it actually take to fix different classes of issues?
✅ Build fast lanes for KEVs and high-exposure components
✅ Automate where possible — especially triage, routing, and SLA monitoring
✅ Track everything — remediation is compliance, and compliance is risk
9. Where Averlon Fits In
Averlon helps security teams modernize the vulnerability triage and remediation process, translating detection to action — without guesswork.
Our RemediationOps platform combines:
- Exploitability and applicability analysis
- Attack chain-based prioritization
- Remediation planning and automation
- Human-in-the-loop controls
It’s how modern teams make continuous vulnerability management practical — by focusing efforts where it actually matters.
10. Final Thought: Don’t Just Detect Faster — Fix Smarter
FedRAMP’s RFC 0012 isn’t just a policy proposal — it’s a mirror held up to how remediation actually works (or doesn’t). It forces a better question: not what are we exposed to? but what are we doing about it — and how fast?
We encourage every team to read the RFC, submit feedback before August 14, and take this moment to modernize their approach. Because the future of federal cybersecurity won’t be defined by what we find — but how quickly we fix it.
Featured Blog Posts
Explore our latest blog posts on cybersecurity vulnerabilities.
Ready to Reduce Cloud Security Noise and Act Faster?
Discover the power of Averlon’s AI-driven insights. Identify and prioritize real threats faster and drive a swift, targeted response to regain control of your cloud. Shrink the time to resolution for critical risk by up to 90%.